Automated, Scalable, and Accurate Security Testing
Probely’s trusted DAST scanner automates and scales web application and API security testing.
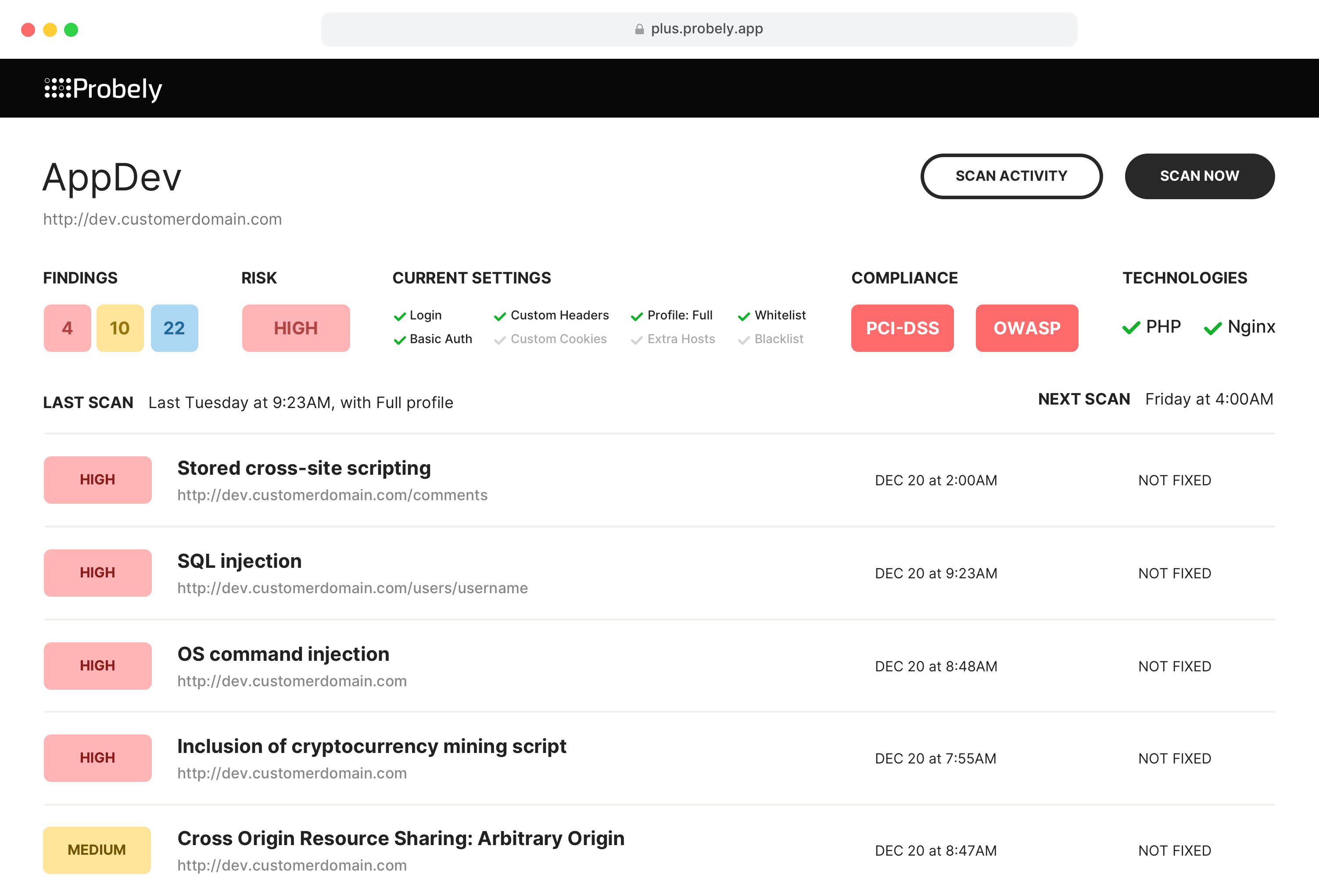
Continuously Raising the Bar in Security Testing
Reduce Cyber Security Risk
Probely’s web application and API vulnerability scanner is able to detect over 30,000 potential vulnerabilities and provides a report of the findings with detailed instructions on how to fix them. Get the security vulnerabilities that matter, false positive free - 0.06% in 2022.
Probely automates security testing in the most efficient way by integrating security testing into your software development lifecycle processes, from your CI/CD tool to your issue tracker, narrowing the gap between development, security, and operations.
No matter your job function, department, or team, Probely can help you work towards reducing your cyber security risk with efficiency and speed.
Powerful Web Application Scanning
Benefit from using features such as customizable scanning configurations, scheduled scanning, partial scanning, scanning behind the firewall, and set blackout scanning periods. You can also perform authenticated scans allowing you to scan applications that use SSO, OpenID Connect, and support for re-authentication if the session is lost.
Our powerful scanner utilizes an innovative headless-Chrome based spider that mimics human behavior by navigating through a web application by clicking links, and filling out forms with the correct context. It supports rich JavaScript apps by listening for events, as well as supporting shadow DOM, pushState, and Hashchange. Get the best coverage in the industry out of the box by crawling every corner of your web application; without human intervention.
Modern API Vulnerability Scanning
Probely’s top-notch API vulnerability scanner is able to detect large amounts of potential vulnerabilities allowing your team to actively run security testing as part of their API development process, no matter how you operate.
If you have a Single-Page Application (SPA) that makes XMLHttpRequests (XHR) to an API, Probely will seamlessly follow those requests and scan the API endpoints. If instead, you want to scan standalone APIs, you can do so via providing OpenAPI/Swagger schema files or Postman Collections.
Find the important issues you need to fix in your APIs by running scans designed to mimic hacking techniques, with detailed instructions on how to fix vulnerabilities.
Automate your Security Testing at Scale
As your company or team grows, so does the pressure to secure critical web assets that could potentially leave your organization exposed. Agile development triggers more frequent releases and automation in the release process in which security should be a part of. Automate security testing into your CI/CD pipeline with Probely.
At Probely we focus on the efficiency of the process — independently if you integrate Probely into your CI/CD pipelines, or schedule recurring scans of your apps. From detection to remediation, Probely can efficiently help your company scale application security testing.
Security should be at the core of your organization without compromising valuable time and resources; whether you have one web application, or five thousand.
Get the security vulnerabilities that matter
Benefit from our industry-low false positive rate
False positives could be time consuming to handle, resulting in wasted time and resources from your security team. Probely’s web vulnerability and API scanner delivers near-zero false positives (0.06%), ensuring that detected vulnerabilities are a real threat and need to be addressed.
Our team has dedicated years of work towards perfecting our industry-low false positive rate. We continuously improve by analyzing every report our customers file, while bookmarking the results we encounter.
What are the consequences of having too many False Positives?
- “Alert fatigue” from your team: Your team will get an alert thinking it’s real, wasting time working on it.
- If you use a tool that delivers many false positives it results in the need of your team validating each and every vulnerability reported.
- Finally, your team has lost confidence in the tool and its validity.
Scanning in the CI/CD pipeline and DevSecOps
Probely is designed to empower Security and DevOps teams to work efficiently together on a DevSecOps approach, built to reduce risk across web applications and APIs.
Build security automation into every step of your SDLC – so your teams can eliminate hundreds of hours of manual tasks in their daily work, saving money and reducing cybersecurity risk sooner on the software development lifecycle.
Use Probely to fulfill web security compliance requirements
Probely provides an easy and effective way to comply with the requirements related to application security testing of PCI-DSS, SOC2, HIPAA, ISO27001, GDPR, and other local-specific privacy acts standards using a series of detailed requirement reports that can be used as evidence to showcase your compliance.
Probely can help you to save resources by automating security testing of your web applications and APIs to identify evidence-based vulnerabilities and get guidance on how to fix them.
Integrate with your stack
Seamlessly integrate Probely with your tools by using our addons or full-featured API.
“Probely advocates to build security into the CI/CD process, products, and integrate with tools or services your development teams already use.”
Embrace a Continuous Security Culture
Get everyone working on web application and API security
From Development to DevOps, we believe security is the binding value across all teams. Build a unique security experience and culture within your organization.
Improve cross-team collaboration
Security is the common ground where Development and Security teams can work together to find and fix vulnerabilities – fast.
Enable continuous improvement
Application vendors must translate security values into actions. Empower your teams to tackle the high-risk vulnerabilities. Dispense with the barriers that get in the way of action.
Ready to get started?
Join the growing community of organizations that rely on Probely for their continuous security testing.